Fox News Flash top headlines for Nov. 8
Fox News Flash top headlines for Nov. 8 are here. Check out what's clicking on Foxnews.com
Malware creators are getting political, using President Trump's likeness as bait for victims.
The applications tap into opinions about political figures with a special focus on Trump, according to Cisco Talos, a threat intelligence firm.
Talos discovered ransomware, screenlockers, remote access trojans (RATs) and other software that play off of Trump as well as other high-profile politicians like Hillary Clinton and Vladimir Putin.
FBI WARNS OF NEW CYBER THREAT TO US THAT INVOLVES 'WHOLE VARIETY' OF ACTORS FROM CHINA
In many cases, “it is clear that the authors of these applications were motivated by their political beliefs,” according to Talos in a blog post.
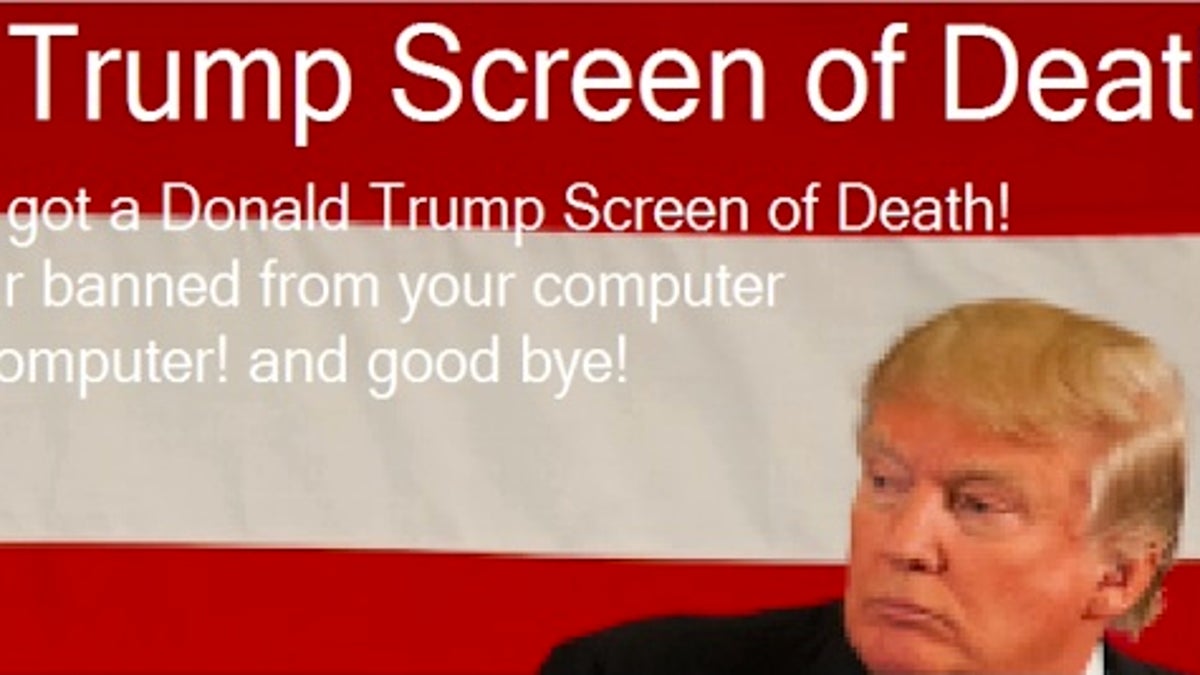
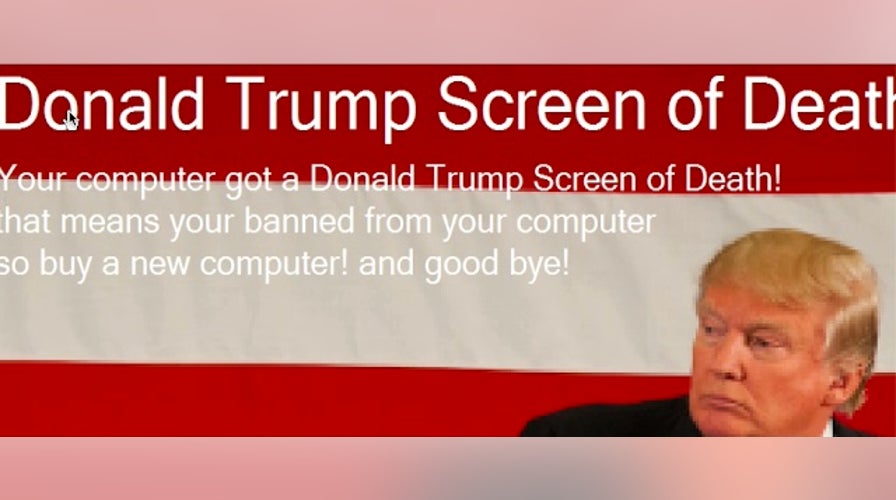
Screenshot of the 'Donald Trump screen of death'. (Cisco Talos)
One application was called “This is the Donald Trump Ransomware” and another “Putin Lockware 2.0.”
Screenlockers – a kind of a poor man’s ransomware that does not encrypt files – removes the icons, taskbar, and task manager on the victim’s machine and “locks” the computer, with the screenlocker’s graphics taking over the entire display.
RUSSIAN HACKERS ON THE ATTACK BECAUSE OF POSSIBLE OLYMPIC BAN
“These steps are performed in an attempt to make exiting the application difficult for victims and maximizes the likelihood of a successful ransom payment,” Talos said.
The ransomware and screenlockers discovered by Talos sometimes didn’t work and seemed to be more effective as political triggers and getting the victim to “click because their opinion on the matter is so strong,” Craig Williams, director of Talos Outreach, told Fox News.
A Trump-themed screenlocker required the victim to click a button displayed in the locker application window. The final lock screen, called the "Donald Trump Screen of Death," is a play on the Windows Blue Screen of Death (BSD), which implies the system has been locked.
HACKERS ARE DRAINING ATMS ACROSS THE US
But the software was more political show than actual malicious software. “If you clicked on the screen, the locker was removed, and the system appeared to operate normally,” Talos said.
But others were malicious. An xls, or Excel spreadsheet, file titled, "Trump administration economic indicators on China investments" contained malicious macros – a sequence of computer operations – meant to infect systems with PoisonIvy, a remote access tool that has been used by cyberespionage groups in the past, according to Talos.
In another case, a so-called crypter displayed iconography associated with Trump. Crypters are commonly used to evade antivirus detection by encrypting or hiding the malicious code associated with malware binaries, according to Talos.
MASSIVE SEXTORTION ATTACK RUNNING WILD, SECURITY FIRM SAYS
Yet another was called "Trump's Cyber Security Firewall," which was focused on hardening Windows systems.
CLICK HERE TO GET THE FOX NEWS APP
“When the user clicks the ‘Build the wall!’ button, the system does some basic hardening, including activating the system's firewall and then requests a reboot,” according to Talos.