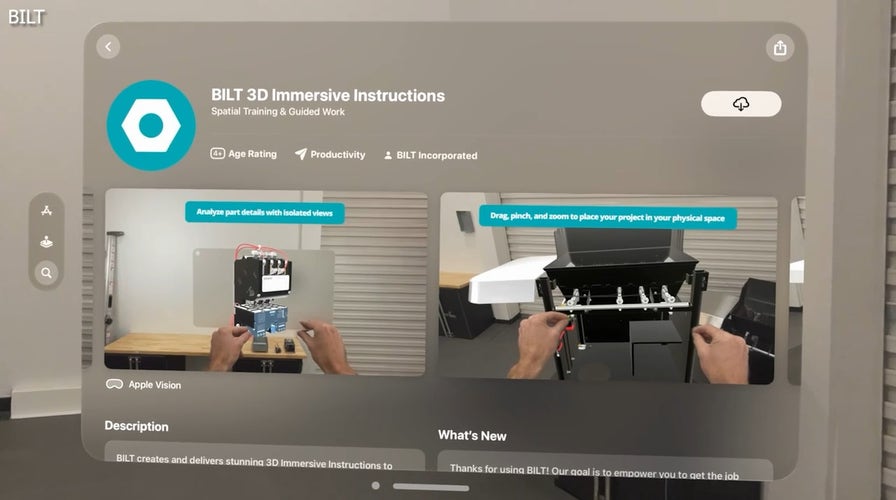
'CyberGuy': Never fumble through paper instructions ever again with this killer Apple Vision Pro 3D app
Kurt Knutsson gives the details on BILT's new app for Apple Vision Pro that provides 3D immersive instructions to make DIY projects easier, faster and more enjoyable.
X – formerly known as Twitter – has gone through more than a name change since it switched over. One of these has been with the account verification process. You know, that little blue check mark that certain profiles have that indicates it's verified. Without that blue check mark, it can be difficult to contact other people on X, get through certain groups and, essentially, use the platform to the fullest.
It's no surprise that this little blue check mark has spurred a lot of controversy. But it's not just this. The changes going on with X's verification – aka X Premium or Premium+ – also open a whole new can of worms, specifically when it comes to cybersecurity concerns.
X blue check-mark verification (X) (Kurt "CyberGuy" Knutsson)
How does one get a verified, blue check mark on X?
Before Elon Musk took over Twitter, there was only one way to get the blue check mark – or Twitter Blue – on Twitter. To do so, you had to be a well-known figure like a celebrity, politician, journalist or part of an organization. Generally, Twitter would reach out to the person directly to confirm their identity.
Now, that's all changed. These days, just about anyone can get a blue check mark via X's subscription-based model if they're willing to pay a monthly subscription fee. (And paying more can also get you a gold check mark, which is usually reserved for businesses.)
This fee not only gets you verified but also gives you the ability to do things on X that those without it can't, like editing tweets, exposure to fewer ads and possibly more visibility for your tweet. Some accounts have even enabled a setting to only be able to receive messages from verified accounts.

X gold check-mark verification (X) (Kurt "CyberGuy" Knutsson)
MORE: TIPS TO FOLLOW FROM ONE INCREDIBLY COSTLY CONVERSATION WITH CYBERCROOKS
How scammers are taking advantage of X's verification-change chaos
Unfortunately, there is a downside to everyone being able to get that blue check mark. Not only do you now have to be concerned with getting yourself verified so that you can direct message others who have that setting enabled, but you also have to be on the lookout for scammers who are using the blue check mark to trick you. Here are three scams to look out for.
1) Blue-tick scammers
A blue-tick scammer is a person who pays to get the blue-tick check mark verification on X and then uses that to scam people. But who do they scam and how? Blue-tick scammers have a very particular method and usually target users who complain about poor customer service on X. Maybe they are even complaining specifically about the issues getting their verification on X.
Ultimately, the goal of these scammers is to trick you into disclosing your bank details by promising refunds to you. In June of last year, for example, passengers whose EasyJet flights had been canceled were targeted by cybercriminals on X in this exact way. These scammers were using fake profiles to target victims who had resorted to X to voice their complaints against the airline and demand a refund, only to potentially lose more money by being scammed.
2) Elon Musk impersonators
It’s not uncommon to encounter fake accounts pretending to be well-known personalities – even Elon Musk. These accounts might lack official verification, but at first glance, they won't give unsuspecting users a reason to doubt that the profile is who it appears to be. These Elon Musk impersonators will try just about anything, but a popular scam is in the form of cryptocurrency ads.
Here's how the scam goes down. An ad appears on X, which appears to be coming from one of Elon Musk's companies – or a blue-tick verified Elon Musk profile – advertising a new cryptocurrency that he's created and steps for people to get it, ultimately encouraging you to transfer money over to the scammer's wallet.
Elon Musk's official X account (X) (Kurt "CyberGuy" Knutsson)
MORE: PROTECT YOUR BACON: THE RISE OF PIG BUTCHERING SCAMS AND HOW TO AVOID THEM
3) Bots posing as scantily clad women
Not everyone will fall for this one, but it's a scam as old as time that's adapted to new rules on social media environments. If you get any direct messages from verified X accounts posing as a scantily clad woman, it could be a legitimate user. But, it could also be a scammer or even a "sexbot," which has increased in numbers since all the changes at X as well as the introduction of AI.
I don't use X. Why should I be concerned?
The changes on X highlight wider issues in online verification and the potential for misuse. Even if you don't use X, scammers may attempt similar tactics on other platforms you frequent. Being aware of these scams and how they work can help you stay safe online.

X gold check-mark verification (X) (Kurt "CyberGuy" Knutsson)
How to stay safe from blue check-mark scammers
The good news is that X is aware of these scams. Now, X's non-deceptive Twitter eligibility requirements for buying a Premium subscription require the user to not have recently changed their photo, display name or username. One of the best ways to protect yourself from scams on popular social media platforms like X is to simply be aware of what new scams are out there. By staying up to date, you can know your weapon to ward off these scammers.
That being said, there are 10 steps you can take to ensure your safety on X.
1) Protect your personal information: Do not share your full name, address, phone number, email, passwords or other sensitive information with strangers or people you do not trust on X.
2) Be skeptical: If an X account seems fishy, investigate further. Check join dates, usernames and their activity history.
3) Use a unique and strong password for your account and change it regularly: Consider using a password manager to securely store and generate complex passwords. It will help you to create unique and difficult-to-crack passwords that a hacker could never guess.
4) Enable two-factor authentication: Two-factor authentication is just an extra shield that will prevent a hacker from getting into your accounts. 2FA requires you to enter a code that is sent to your phone or email or generated by an app in addition to your password when you log in. This way, even if someone knows your password, they cannot access your account without the code.
5) Review your privacy settings: Limit who can see your posts, photos and profile information on X by changing your privacy settings.
6) Verify the source and accuracy of information: Do not believe everything you see or read on social media. Always check the source and credibility of the information before you engage with the content and share it with others. Use reliable and reputable sources to verify the source and the facts.
7) Have good antivirus software on all your devices: The best way to protect yourself from having your data breached by a scammer on X is to have antivirus protection installed on all your devices. Having antivirus software on your devices will make sure you are stopped from clicking on any potential malicious links, which may install malware on your devices, allowing hackers to gain access to your personal information. Get my picks for the best 2024 antivirus protection winners for your Windows, Mac, Android & iOS devices.
8) Delete anyone who tries to trick you: If anyone tries to scam you, or you encounter any suspicious accounts, consider reporting them to X immediately. You can use X’s reporting features to flag potential scams. This will also help others from being scammed.
9) Stay informed about security updates: Keep your software and apps updated to protect yourself from the latest threats.
10) Prevent strangers from following you, via X's privacy settings: This can be a good way to prevent some of those bots or scammers from getting to you.
All you need to do is click on Settings, select Privacy and Safety, move the toggle for Protect Your Tweets and select Done. Now, only people whose accounts you approve have permission to follow you. You can also block and remove followers if the former is too strict for you.
MORE: HOW TO PROTECT YOURSELF FROM SOCIAL MEDIA SCAMMERS
Kurt's key takeaways
Social media can be like the Wild West, especially when a bunch of new changes are happening every day. In terms of cybersecurity and protecting yourself online, it's important to be aware of scams like this. Just because something has a blue check mark (or, anything else that would make it seem "verified" in a certain context) does not mean that it is. It's so easy for scammers to pose as someone or something else, and chances are they'll keep coming along. So, it's OK to second-guess something if you're not 100% sure; and online, we never really can be.
What are your biggest concerns about the potential for scams on the social media platforms you frequently visit? Let us know in the comments below. Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips & security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you'd like us to cover.
Answers to the most asked CyberGuy questions:
- What is the best way to protect your Mac, Windows, iPhone and Android devices from getting hacked?
- What is the best way to stay private, secure and anonymous while browsing the web?
- How can I get rid of robocalls with apps and data-removal services?
Copyright 2024 CyberGuy.com. All rights reserved.