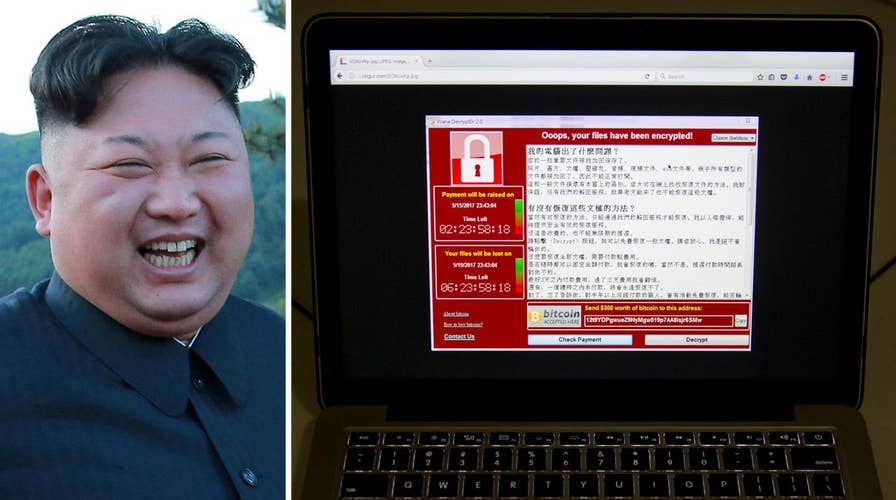
Last week’s global cyber attack has shed light on the shadowy and highly sophisticated team of cyber spies in North Korea believed to be among the best hackers in the world.
That elite and highly trained team is believed to be behind the biggest online extortion attack ever – it held more than 300,000 computers in 150 countries for ransom and crippled several European companies and U.K. hospitals.
While the Hermit Kingdom is often the subject of mockery when it comes to its frequently-unsuccessful missile tests, last week's hack may simply be the latest sign of Pyongyang's prowess on the digital battlefield.
NORTH KOREA POSSIBLY BEHIND GLOBAL CYBERATTACK, RESEARCHERS SAY
Digital security stalwarts Symantec and Kaspersky Lab are now reporting that the software used in last week's attack, known as WannaCry, includes a portion of code that has been used by hackers known as the Lazarus Group. Kaspersky, which has been monitoring the group for years, says that the links between the hacking collective and North Korea are undeniable.
The similarity between the WannaCry code and the code used by Lazarus hackers was reportedly first noticed by a security researcher with Google. And while there are concerns that the individuals behind WannaCry may have included this bit of code to trick investigators, North Korea and the group to which they are being linked, have quite a resume when it comes to aggression in cyberspace.
'Among the best in the world'
A 2013 Department of Defense report suggests the sluggishness of North Korea's economy may be the reason why they are pursuing operations in the digital space, and that "[offensive cyber operations] may be seen as a cost-effective way to develop asymmetric, deniable military options."
Cost-effectiveness aside, experts agree that the Hermit Kingdom's cyber capabilities are undeniable. In April 2016, Army Gen. Vincent K. Brooks, now the commander of U.S. forces in Korea, told the Senate Armed Services Committee that the North Koreans "are among the best in the world and the best organized" when it comes to cyber threats.
US ENVOY: NORTH KOREA IS INTIMIDATING THE ENTIRE WORLD
Experts have previously attributed some of North Korea's alleged cyber exploits to a group of highly-trained cyber spies known as "Bureau 121," a group that Reuters has previously described as a "handpicked, pampered elite." An expert who claimed to have studied with members of Bureau 121 told Reuters that the military hackers are some of the most talented members of the Hermit Kingdom, and some of the best rewarded.
South Korea has claimed that the North's digital army could number as many as 6,000, a number confirmed by a North Korean defector in a 2015 BBC interview.
That same defector, Professor Kim Heung-kwang, suggests that Bureau 121 was established decades ago, and initially began in China. Experts believe that North Korea continues to conduct illicit activities in China, though Kim suggests China-based operations have been scaled back significantly. He added in an interview with CNN that some of his own students wound up becoming cyber warriors for the Hermit Kingdom.
NORTH KOREA'S CLOSEST MAJOR US CITY, SEATTLE, WANTS TO PLAN FOR POSSIBLE NUCLEAR ATTACK
The Lazarus Group
Just last month, researchers with Kaspersky for the first time discovered what they called "a direct link" between the hacker collective dubbed the Lazarus Group and North Korea. They wouldn't say that the link confirmed North Korea was behind all of the exploits attributed to Lazarus, though, of which there have been plenty.
The Lazarus Group has been linked to last year's $81 million digital heist from the Federal Reserve Bank of New York. The hackers had apparently attempted to steal even more, some $951 million. NSA Deputy Director Rick Ledgett has reportedly argued that if North Korea had anything to do with the attack, "that means that a nation state is robbing banks," something he calls "a big deal."
Lazarus was also implicated in the 2014 attack on Sony Pictures Entertainment after an international consortium of security researchers launched an investigation they dubbed "Operation Blockbuster." According to the group's findings, Lazarus has "been active since at least 2009, and potentially as early as 2007.”
According to the Novetta Threat Research Group, "from the 2009 DDoS attacks, to the Ten Days of Rain attacks and Operation Troy, a cyber espionage campaign that reportedly culminated in the March 2013 DarkSeoul attack, the Lazarus Group has been carrying out a series of attacks with the tools identified during Operation Blockbuster."
Kaspersky researchers describe the scale of the Lazarus Group's operations as "shocking," and suggested the "rare cases when they are caught [using the same kind of code twice] are operational mistakes, because the group seems to be so large that one part doesn’t always know what the other is doing."