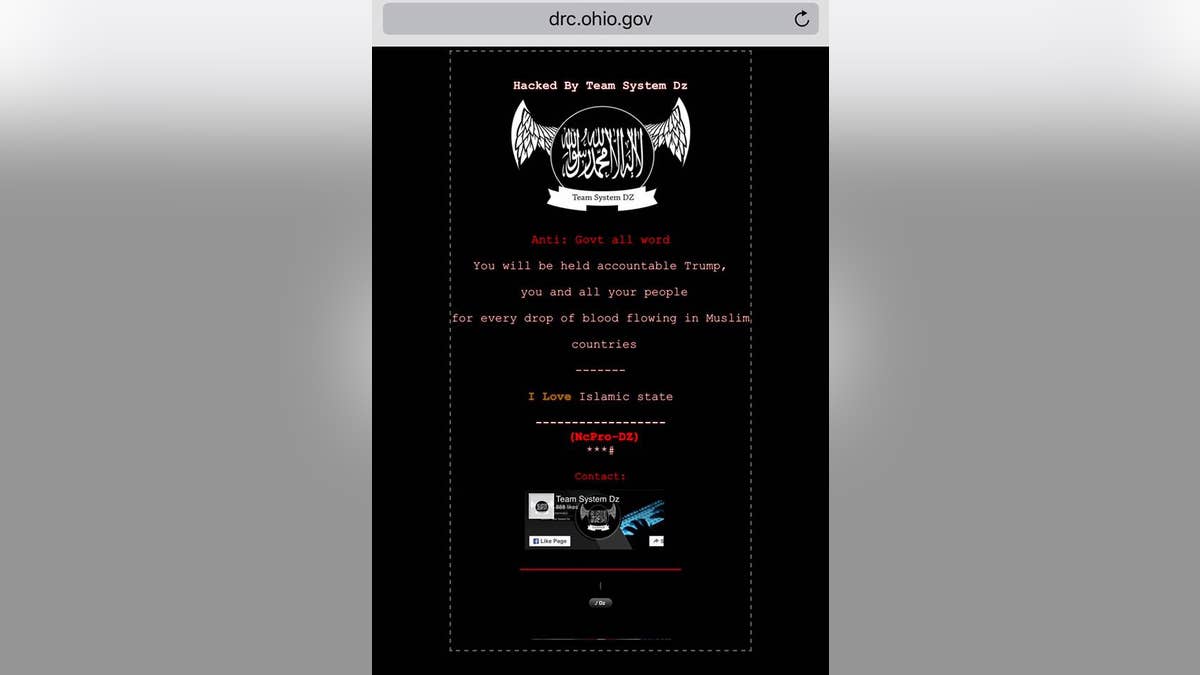
The Ohio Department of Corrections website, which was defaced on June 25, 2017.
The latest target of pro-ISIS hackers is none other than 800 school websites across the United States.
The widespread hack occurred last Monday, and lasted two hours, in which visitors were redirected to a YouTube propaganda video featuring Arabic audio, the text, “I love Islamic State (ISIS)” and images of former Iraqi dictator Saddam Hussein.
“Unless we have irrefutable evidence to suggest otherwise, we need to assume confidential data has been compromised,” Hamid Karimi, vice president of business development and the security expert at Beyond Security. “That should be a cause for concern. To remedy the situation, all schools and institutions that serve minors must submit to (a) stricter set of cybersecurity rules.”
The breached school websites, which spanned nationwide from New Jersey to Arizona and Virginia to Connecticut, are all powered by a company called SchoolDesk. The company since has handed over its server — which runs out of Georgia — to the FBI for investigation and also has hired external security firms to trace the hackers. The Atlanta-based company said after the hack that technicians detected that a small file had been injected into the root of one of its websites.
“The websites were redirected to an iframed YouTube video. No data was lost or altered in any way. Because we’re currently working with the FBI in an active investigation of this incident, as well as forensic team from Microsoft, we cannot yet discuss any technical details or exact methods of access to SchoolDesk’s network or software,” a spokesperson for SchoolDesk told Fox News.
The company has insisted that no personal or student information was exposed, but some security experts say the matter should be closely monitored, especially as minors are involved.
“In most hacks, organizations do not have full visibility into what happened or what information was compromised,” surmised Eric Cole, who served as commissioner on cyber security for President Barack Obama, and was formally a senior vice president at MacAfee and the chief scientist at Lockheed Martin. “In almost every breach, what is initially reported is usually extremely conservative and over the weeks following a breach, it is always worse than what was originally reported.”
The proud culprits of the hack? A shadowy pro-ISIS hacktivist outfit known as “Team System DZ.”

A man types on a computer keyboard in Warsaw in this February 28, 2013 illustration file picture. One of the largest ever cyber attacks is slowing global internet services after an organisation blocking "spam" content became a target, with some experts saying the disruption could get worse. To match INTERNET-ATTACK/ REUTERS/Kacper Pempel/Files (POLAND - Tags: BUSINESS SCIENCE TECHNOLOGY) - RTXXZVX (Reuters)
Lorraine Murphy of The Cryptosphere, a specialist hacking and malware news site, which long has been tracking Team System DZ, said that the group generally speaking is focused on “making public deface” rather than penetrating systems and getting information, and has been in-motion pre-dating ISIS, going back to at least 2013.
“They used to support freedom for Palestine, #OpFreeGaza, and freedom for Kashmir, and now they support ISIS,” Murphy said. “Team System DZ basically has one trick: take advantage of outdated WordPress sites, and make bold, scary-looking defaces. It’s a trick that has been working for them for three years, and there is no reason to believe that it will stop working anytime soon.”
Over the course of more than three years, the group has hacked vast and a seemingly arbitrary range of thousands of websites across the world — from scores of U.S. government sites including the Washington State Department of Health, the Ohio Department of Administrative Services and the Howard County, Maryland government site, which were replaced with a black screen, Islamic calligraphy, the Call to Prayer and the words: “You will be held accountable, Trump, you and all your people every drop of blood flowing in Muslim countries.” Canada’s Prince Albert police station also was targeted last week, and the city council in Aberdeen, Scotland, and even a local West Yorkshire, England rugby team have been apprehended in the past.
“The wide range of targets all had one common characteristic: they had weak network and web protection,” Karimi pointed out. “It appears that Team DZ was acting opportunistically as opposed to surgically.”
'JIHADI COOL': HOW ISIS SWITCHED ITS RECRUITMENT AND SOCIAL MEDIA MASTER PLAN
Cyber forensic data has indicated that the attacks waged by the group initially came from Algeria, also indicated by the use of the “DZ,” which is the country’s internet domain code.
However, it is likely that they have franchised their defacing operations without a central command, Harimi explained, thus have become both global and difficult to track. For example, Alex Kassirer, director of counterterrorism at intel firm Flashpoint, told Fox News that the group is known to have at least one member from Jordan based on the actor’s pseudonym “zilzal jordan,” with zilzal being the Arabic word for earthquake.
“The threat they pose is largely limited to the propaganda and messaging war,” she continued.
The FBI long have been reported to be investigating the notorious Team System DZ, but declined to comment on the matter. It is believed that no one directly part of the sympathizer hacking group, despite how long they have been operating, are believed to ever have been made.

ISIS has long waged a recruitment and propaganda war online. (Reuters)
“What they typically do is cyber-graffiti, they are attempting to spread propaganda on behalf of ISIS to garner support,” noted Dan McNemar, director of threat intelligence at Binary Defense Systems. “A number of pro-ISIS groups have come and gone, Team DZ has certainly been around the longest.”
But alliance ties between Team System DZ and ISIS itself remain murky. To date, ISIS has not formally acknowledged the group or indicated they have any authority over the cyber outfit. Yet as long as such hacking groups remain unscathed, so too does the propaganda and recruitment machine — along with their potential to go beyond the realm of website defacement.
“They have not been arrested primarily because they are a low-level operator that is more nuisance than genuine threat at this point. Why waste time on a web defacer, when we can spend time on high value targets instead? But we should be thinking about how these attacks could ‘evolve’ in the future,” added Jeff Bardin, chief information officer of Treadstone 71, a security firm specializing in cyber-threat intelligence and analyzing online jihadists and extremist groups. “To go beyond mere propaganda into more serious territory like cyber extortion and threats.”








































