Unclear whether money was motive behind Petya malware
Some analysts think hackers wanted to disable computer systems in Ukraine; reaction from cybersecurity expert Leeza Garber
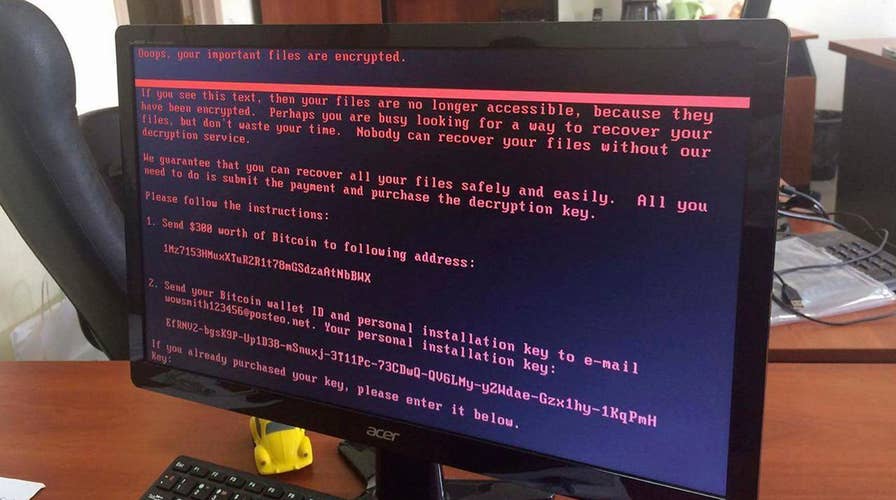
Security experts say that a digital "vaccine" can protect individual computers from the crippling Petya ransomware.
Petya sparked mass disruption after it emerged Tuesday. Ukraine and Russia appeared hardest hit by the new strain of ransomware — malicious software that locks up computer files with all-but-unbreakable encryption and then demands a ransom for its release. In the U.S., the malware affected companies such as the drugmaker Merck and Mondelez International, the owner of food brands such as Oreo and Nabisco.
Cybereason security researcher Amit Serper found a way to prevent the ransomware affecting computers, according to the Bleeping Computer security news site, which notes that other experts agreed with his findings. Users can create a read-only file called ‘perfc’ in their C:/Windows folder to ‘vaccinate’ their computers and stop Petya.
However, while this approach can stop the ransomware on individual computers, experts have not yet found a so-called “kill switch” that would completely stop the ransomware attack.
HUGE 'PETYA' RANSOMWARE ATTACK HITS EUROPE, SPARKS MASS DISRUPTION
Petya’s pace appeared to slow as Tuesday wore on, in part because the malware appeared to require direct contact between computer networks, a factor that may have limited its spread in regions with fewer connections to Ukraine.
The malware's origins remain unclear. Researchers picking the program apart found evidence its creators had borrowed from leaked U.S. National Security Agency code, raising the possibility that the digital havoc had spread using U.S. taxpayer-funded tools.
Symantec Security Response reported Tuesday that the latest round of ransomware is harnessing the same EternalBlue Windows exploit as the WannaCry ransomware that wreaked havoc across the globe last month.
Microsoft issued a patch for EternalBlue in March.
22-YEAR-OLD CYBERSECURITY RESEARCHER HELPED THWART UNPRECEDENTED CYBERATTACK
Experts say that Petya highlights the need for organizations to keep their systems up to date with the latest security measures.
“It’s alarming that we’re seeing another large-scale, global ransomware attack on the heels of the recent WannaCry incident,” said Varun Badhwar, CEO and co-founder of cloud security company, RedLock, in a statement emailed to Fox News. “Every company and consumer connected to the internet needs to immediately install the patch that Microsoft released back in March to fix the EternalBlue vulnerability that the new Petya ransomware attack is leveraging. For companies that forego implementing the latest security patches and updates, vulnerabilities like EternalBlue are ticking time bombs.”
“The recent attacks associated with WannaCry and Petya have re-enforced the lack of accountability and focus on basic IT and security fundamentals,” added James Carder, chief information security officer LogRhythm, in a statement emailed to Fox News. “Core IT operational competencies, such as patch management, backups, disaster recovery, and incident response are not well implemented or maintained.”
On Wednesday, the mysterious Shadow Brokers group also re-emerged to taunt the NSA. It's a possible hint at the shadowy spy games being played behind the scenes of the cybersecurity crisis.
RANSOMWARE ATTACK COSTS SOUTH KOREAN COMPANY $1M, LARGEST PAYMENT EVER
The Shadow Brokers, who have spent nearly a year publishing some of the American intelligence community's most closely guarded secrets, posted a new message to the user-driven news service Steemit carrying new threats, a new money-making scheme and nudge-nudge references to the ransomware explosion that continues to cause disruption from Pennsylvania to Tasmania.
"Another global cyber attack is fitting end for first month of theshadowbrokers dump service," the group said, referring to a subscription service which purportedly offers hackers early access to some of the digital NSA's break-in tools. "There is much theshadowbrokers can be saying about this but what is point and having not already being said?"
The Associated Press contributed to this article.
Follow James Rogers on Twitter @jamesjrogers